반응형
Kubenetes Dashboard 설정
쿠버네티스 활성화
docker desktop을 켜고 설정에서 쿠버네티스를 체크하여 활성화 시켜준다.

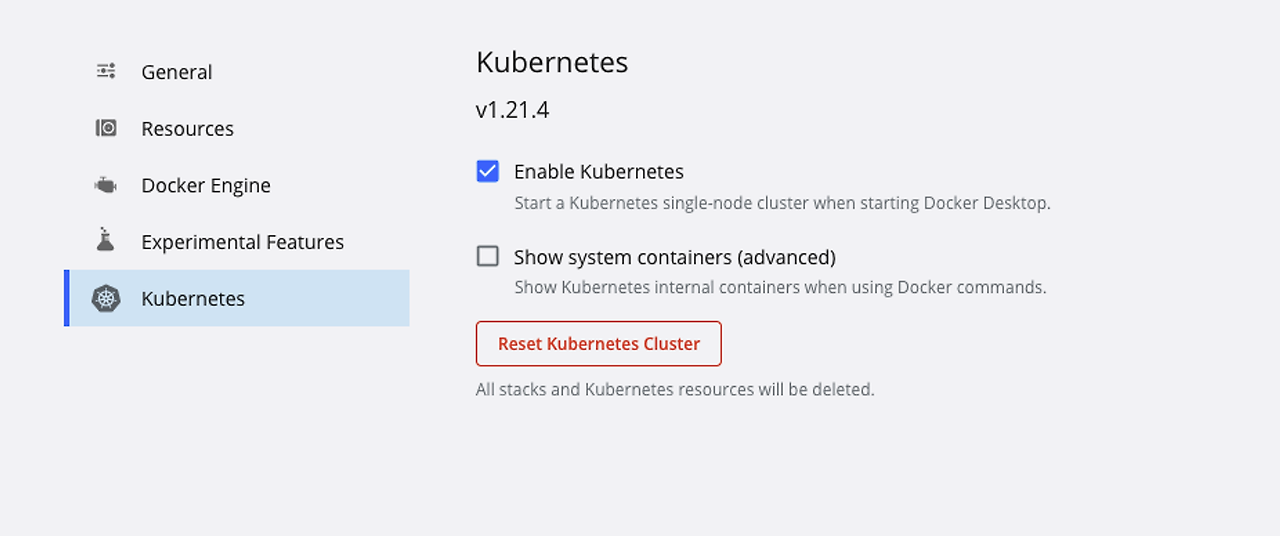
쿠버네티스가 활성화 되었는지 확인해본다.
mezzo-skan@mezzoui-MacBookPro ~ % kubectl cluster-info
Kubernetes control plane is running at https://kubernetes.docker.internal:6443
CoreDNS is running at https://kubernetes.docker.internal:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy
To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'.
mezzo-skan@mezzoui-MacBookPro ~ %쿠버네티스 대시보드 활성화
대시보드 배포
mezzo-skan@mezzoui-MacBookPro ~ % kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.6.1/aio/deploy/recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
mezzo-skan@mezzoui-MacBookPro ~ %쿠버네티스 대시보드를 배포하고 접속하기
웹 UI(쿠버네티스 대시보드)를 배포하고 접속한다.
kubernetes.io
프록시 띄우기
다음 명령어로 로컬에서접속 가능한 프로시를 생성해준다.
nohup kubectl proxy
or
nohup kubectl proxy --port=8001 --address=192.168.1.10 --accept-hosts='^*$' >/dev/null 2>&1 &UI 접근
http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/데시보드 정보 확인
서비스 어카운트를 통해 계정들을 확인 할 수있다.
하단에 보면 대시보드와 관련된 계정을 확인 할 수 있다.
kubectl get serviceaccounts -A
NAMESPACE NAME SECRETS AGE
default default 1 22h
kube-node-lease default 1 22h
kube-public default 1 22h
kube-system attachdetach-controller 1 22h
kube-system bootstrap-signer 1 22h
kube-system certificate-controller 1 22h
kube-system clusterrole-aggregation-controller 1 22h
kube-system coredns 1 22h
kube-system cronjob-controller 1 22h
kube-system daemon-set-controller 1 22h
kube-system default 1 22h
kube-system deployment-controller 1 22h
kube-system disruption-controller 1 22h
kube-system endpoint-controller 1 22h
kube-system endpointslice-controller 1 22h
kube-system endpointslicemirroring-controller 1 22h
kube-system ephemeral-volume-controller 1 22h
kube-system expand-controller 1 22h
kube-system generic-garbage-collector 1 22h
kube-system horizontal-pod-autoscaler 1 22h
kube-system job-controller 1 22h
kube-system kube-proxy 1 22h
kube-system namespace-controller 1 22h
kube-system node-controller 1 22h
kube-system persistent-volume-binder 1 22h
kube-system pod-garbage-collector 1 22h
kube-system pv-protection-controller 1 22h
kube-system pvc-protection-controller 1 22h
kube-system replicaset-controller 1 22h
kube-system replication-controller 1 22h
kube-system resourcequota-controller 1 22h
kube-system root-ca-cert-publisher 1 22h
kube-system service-account-controller 1 22h
kube-system service-controller 1 22h
kube-system statefulset-controller 1 22h
kube-system storage-provisioner 1 22h
kube-system token-cleaner 1 22h
kube-system ttl-after-finished-controller 1 22h
kube-system ttl-controller 1 22h
kube-system vpnkit-controller 1 22h
kubernetes-dashboard default 1 21h
**kubernetes-dashboard kubernetes-dashboard 1 21h**describe 명령으로 자세한 정보 확인
mezzo-skan@mezzoui-MacBookPro ~ % kubectl describe serviceaccount kubernetes-dashboard -n kubernetes-dashboard
Name: kubernetes-dashboard
Namespace: kubernetes-dashboard
Labels: k8s-app=kubernetes-dashboard
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: kubernetes-dashboard-token-gw2rw
Tokens: **kubernetes-dashboard-token-gw2rw**
Events: <none>
mezzo-skan@mezzoui-MacBookPro ~ %
tokens 값에 대한 name 확인
Token 값 확인
로그인을 하기 위해서는 token 을 알아야지 접근 가능하다.
mezzo-skan@mezzoui-MacBookPro ~ % kubectl describe secret **kubernetes-dashboard-token-gw2rw** -n kubernetes-dashboard
Name: kubernetes-dashboard-token-gw2rw
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard
kubernetes.io/service-account.uid: 668025f6-374d-4046-87cc-2126adb2e53e
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1066 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlliazJXZEdqWnR6cHQtLWhpQWNnSVE5eE4taFU4OHVMMnZaTG54V2tZNm8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1ndzJydyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjY2ODAyNWY2LTM3NGQtNDA0Ni04N2NjLTIxMjZhZGIyZTUzZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.i5RpPtDkrHoaOO2ilkKEgZM9J2zp_FgDgWUYllOnqWGuhs5-6PZtXDfqt0Vl2hYOffwz2bXZ71amXnIdEQA8uqnU6YCEmrCUtX3ApEnkFHDLEjwhQevYrlqskC6BEqbC72sp2hCeFw0z0y0ljqNRQisa6cFPNAIwc-sa-8kmrRPpJw4kfY8eFVTG21jbsJ8rwXiapZ810Q2zjdFKRLGnx8H3m4C_ldiKIMLJe-L5wKsEZhTDc8fRVHU6bBUATmhAG6S2i0Pjaa7FX5w3l8gVUg_oOiXy-VWyFN76geDMCh8vtnDJQXULVfEjNGi6QqmgBYhTGugGE_jLVuWMqqo9ug
mezzo-skan@mezzoui-MacBookPro ~ %토큰값만 확인하기
kubectl describe secret **kubernetes-dashboard-token-gw2rw** -n kubernetes-dashboard | grep token: | awk '{print $2}'해당 토큰 값을 이용하여, 로그인한다.

로그인해서 보면 권한이 없기때문에 메뉴를 눌러도 화면이 보이지 않는다.
데시보드에서 사용자 권한과 관리자 권한을 설정해야한다.

Role 확인 및 권한 설정
권한이 없기때문에 대시보드에서 많은것을 확인 할 수 없다. cluster-admin 권한을 생성하여 admin 권한으로 볼수 있도록 하자
Cluster Role 정보 확인
아무것도 없는것을 확인 할 수 있다.
mezzo-skan@mezzoui-MacBookPro ~ % kubectl describe clusterrole kubernetes-dashboard
Name: kubernetes-dashboard
Labels: k8s-app=kubernetes-dashboard
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
nodes.metrics.k8s.io [] [] [get list watch]
pods.metrics.k8s.io [] [] [get list watch]Role List 확인
여러가지 Role 중에 cluster-admin 을 생성할 것이다.
mezzo-skan@mezzoui-MacBookPro ~ % kubectl get clusterrole
NAME CREATED AT
admin 2023-02-02T08:21:48Z
**cluster-admin 2023-02-02T08:21:48Z**
edit 2023-02-02T08:21:48Z
kubeadm:get-nodes 2023-02-02T08:21:50Z
kubernetes-dashboard 2023-02-02T09:07:50Z
system:aggregate-to-admin 2023-02-02T08:21:48Z
system:aggregate-to-edit 2023-02-02T08:21:48Z
system:aggregate-to-view 2023-02-02T08:21:48Z
system:auth-delegator 2023-02-02T08:21:48Z
system:basic-user 2023-02-02T08:21:48Z
system:certificates.k8s.io:certificatesigningrequests:nodeclient 2023-02-02T08:21:48Z
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 2023-02-02T08:21:48Z
system:certificates.k8s.io:kube-apiserver-client-approver 2023-02-02T08:21:48Z
system:certificates.k8s.io:kube-apiserver-client-kubelet-approver 2023-02-02T08:21:48Z
system:certificates.k8s.io:kubelet-serving-approver 2023-02-02T08:21:48Z
system:certificates.k8s.io:legacy-unknown-approver 2023-02-02T08:21:48Z
system:controller:attachdetach-controller 2023-02-02T08:21:48Z
system:controller:certificate-controller 2023-02-02T08:21:48Z
system:controller:clusterrole-aggregation-controller 2023-02-02T08:21:48Z
system:controller:cronjob-controller 2023-02-02T08:21:48Z
system:controller:daemon-set-controller 2023-02-02T08:21:48Z
system:controller:deployment-controller 2023-02-02T08:21:48Z
system:controller:disruption-controller 2023-02-02T08:21:48Z
system:controller:endpoint-controller 2023-02-02T08:21:48Z
system:controller:endpointslice-controller 2023-02-02T08:21:48Z
system:controller:endpointslicemirroring-controller 2023-02-02T08:21:48Z
system:controller:ephemeral-volume-controller 2023-02-02T08:21:48Z
system:controller:expand-controller 2023-02-02T08:21:48Z
system:controller:generic-garbage-collector 2023-02-02T08:21:48Z
system:controller:horizontal-pod-autoscaler 2023-02-02T08:21:48Z
system:controller:job-controller 2023-02-02T08:21:48Z
system:controller:namespace-controller 2023-02-02T08:21:48Z
system:controller:node-controller 2023-02-02T08:21:48Z
system:controller:persistent-volume-binder 2023-02-02T08:21:48Z
system:controller:pod-garbage-collector 2023-02-02T08:21:48Z
system:controller:pv-protection-controller 2023-02-02T08:21:48Z
system:controller:pvc-protection-controller 2023-02-02T08:21:48Z
system:controller:replicaset-controller 2023-02-02T08:21:48Z
system:controller:replication-controller 2023-02-02T08:21:48Z
system:controller:resourcequota-controller 2023-02-02T08:21:48Z
system:controller:root-ca-cert-publisher 2023-02-02T08:21:49Z
system:controller:route-controller 2023-02-02T08:21:48Z
system:controller:service-account-controller 2023-02-02T08:21:48Z
system:controller:service-controller 2023-02-02T08:21:48Z
system:controller:statefulset-controller 2023-02-02T08:21:48Z
system:controller:ttl-after-finished-controller 2023-02-02T08:21:49Z
system:controller:ttl-controller 2023-02-02T08:21:48Z
system:coredns 2023-02-02T08:21:50Z
system:discovery 2023-02-02T08:21:48Z
system:heapster 2023-02-02T08:21:48Z
system:kube-aggregator 2023-02-02T08:21:48Z
system:kube-controller-manager 2023-02-02T08:21:48Z
system:kube-dns 2023-02-02T08:21:48Z
system:kube-scheduler 2023-02-02T08:21:48Z
system:kubelet-api-admin 2023-02-02T08:21:48Z
system:monitoring 2023-02-02T08:21:48Z
system:node 2023-02-02T08:21:48Z
system:node-bootstrapper 2023-02-02T08:21:48Z
system:node-problem-detector 2023-02-02T08:21:48Z
system:node-proxier 2023-02-02T08:21:48Z
system:persistent-volume-provisioner 2023-02-02T08:21:48Z
system:public-info-viewer 2023-02-02T08:21:48Z
system:service-account-issuer-discovery 2023-02-02T08:21:48Z
system:volume-scheduler 2023-02-02T08:21:48Z
view 2023-02-02T08:21:48Z
vpnkit-controller 2023-02-02T08:22:23Z
mezzo-skan@mezzoui-MacBookPro ~ %모든 리소스에 접근 가능한 관리자 Role 생성
yaml 파일 생성
vi kuebernetes-dashboard-service-account.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kube-system실행
mezzo-skan@mezzoui-MacBookPro ~ % kubectl apply -f kuebernetes-dashboard-service-account.yaml
serviceaccount/admin-user created
clusterrolebinding.rbac.authorization.k8s.io/admin-user created
추가된 서비스 어카운트 정보 확인
mezzo-skan@mezzoui-MacBookPro ~ % kubectl get serviceaccounts -A
NAMESPACE NAME SECRETS AGE
default default 1 22h
kube-node-lease default 1 22h
kube-public default 1 22h
**kube-system admin-user 1 2m29s**
mezzo-skan@mezzoui-MacBookPro ~ % kubectl describe serviceaccount admin-user -n kube-system
Name: admin-user
Namespace: kube-system
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-user-token-kcj2b
Tokens: admin-user-token-kcj2b
Events: <none>
****mezzo-skan@mezzoui-MacBookPro ~ % kubectl describe secret admin-user-token-kcj2b -n kube-system
Name: admin-user-token-kcj2b
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin-user
kubernetes.io/service-account.uid: 5be47e26-d954-4175-942c-d5fa9d2e85cf
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1066 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlliazJXZEdqWnR6cHQtLWhpQWNnSVE5eE4taFU4OHVMMnZaTG54V2tZNm8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLWtjajJiIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI1YmU0N2UyNi1kOTU0LTQxNzUtOTQyYy1kNWZhOWQyZTg1Y2YiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06YWRtaW4tdXNlciJ9.EAqZzjVRPSGrqZ8MAOfXVCgVj8H1gPEg8OVzIX-Z02hoSg86mEoN7A0Iz5U5MDUlk-ITy-FSquLd8XlOIE0XkeL1tbl7wM301lkhHUWOZ4KXW5pw9Z3t45Rso68WWY5ToI_f5IS5Sp8r09l4YEiGaLNvRmlD5T5QWVI5LTB_voyIEkf12BXg8p7OzE43sXs35XM21o-adVcbjEZBWwsybC55WPi6h_dc3Jqu8ChWfrZrmRpDgsgcvdSUdxm3cbdgf74vC0tLKDaZsnfdHPP2HGSHxVjayAFBYS4ctgYILyjiiDRhsSxbthbM25rYr5g-A5pGh42EaAp3rdX1HQwVpw
mezzo-skan@mezzoui-MacBookPro ~ %해당 토큰으로 다시 로그인하면 접근되지 않았던 정보들을 확인해 볼 수 있다.
Dashboard 삭제 하기
삭제할땐 설치했던 버전의 yaml 을 찾아서 다음과같이 실행한다.
kubectl delete -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.6.1/aio/deploy/recommended.yaml결과
mezzo-skan@mezzoui-MacBookPro spring-cloud-template-test % kubectl delete -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.6.1/aio/deploy/recommended.yaml
namespace "kubernetes-dashboard" deleted
serviceaccount "kubernetes-dashboard" deleted
service "kubernetes-dashboard" deleted
secret "kubernetes-dashboard-certs" deleted
secret "kubernetes-dashboard-csrf" deleted
secret "kubernetes-dashboard-key-holder" deleted
configmap "kubernetes-dashboard-settings" deleted
role.rbac.authorization.k8s.io "kubernetes-dashboard" deleted
clusterrole.rbac.authorization.k8s.io "kubernetes-dashboard" deleted
rolebinding.rbac.authorization.k8s.io "kubernetes-dashboard" deleted
clusterrolebinding.rbac.authorization.k8s.io "kubernetes-dashboard" deleted
deployment.apps "kubernetes-dashboard" deleted
service "dashboard-metrics-scraper" deleted
deployment.apps "dashboard-metrics-scraper" deleteddashbord에 접속하기 할때 token 없이 접속하게 할 수있다.
들어갈때마타 토큰을 입력하니 보안이 높아 좋기한데, 불편하기때문에 이를 없애고 접근하게 할수도 있다.
반응형
'devops > Kubernetes' 카테고리의 다른 글
| kubernetes namespage (0) | 2024.04.25 |
|---|---|
| kubernetes service (nodeport) 에대한 설명 (1) | 2024.04.25 |
| kubernetes minikube install (0) | 2024.04.25 |
| kubectl 명령어 (0) | 2024.04.25 |
| Argo CD 설치하기, Argo CD 란? (0) | 2023.04.28 |


